The CyberESI Vulnerability Scanning Subscription service provides you the information you need to secure your organization. Identify and fix holes in your security before an a cyber incident happens to you.
For a monthly fee, CyberESI:
- scans your computers and networks to identify vulnerabilities
- performs Penetration Testing to see if more severe vulnerabilities are likely to result in cyber incidents
Looking for Weaknesses
Vulnerability scans looks for holes in your network firewall, where malicious outsiders can break in and attack your network. External scans look from outside your network, while internal scans operate inside your firewall. Scanning from either point of view identifies both real and potential vulnerabilities that could impact your business.
Testing Defenses
Penetration tests try to actively bypass your security controls and enter your network environment. Testing tactics can include aggressive scanning, network sniffing, social engineering, phishing, and more.
The Importance of Identification
You can’t fix what you don’t know is broken. Knowledge of your network’s strengths and weaknesses enables an on-going understanding of your environment. This insight allows you the opportunity to confirm your assets are protected, or to proactively take action to mitigate any discovered risks.
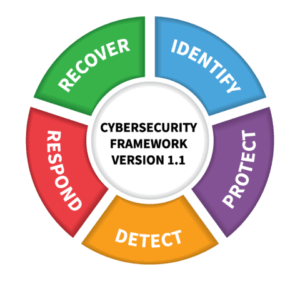 | The NIST Cybersecurity FrameworkVulnerability Scanning and Penetration Testing support the Identify function of the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF). The NIST CSF is the most successful and prevalent approach to cybersecurity risk management in the world. The Functions of CSF – Identify, Protect, Detect, Respond, and Recover – remind us of the need to balance preventative measures with preparations should something go wrong. |
 | Network Defense by Incident RespondersIncident responders – the technologists who swing into action when a cyber incident occurs – are the best in the business at spotting weaknesses cyber threat actors will use to break in to your computers and networks. Much of CyberESI’s workforce previously worked at the acclaimed Defense Cyber Crime Center, successfully responding to both criminal and nation-state incidents. And we still provide incident response services to this day. Let us use our specialized experience to help you secure your organization. |
Typical Subscriptions IncludeExternal Vulnerability Subscription
Internal Vulnerability Subscription
External-Internal Vulnerability Subscription
|
