MDR services augment traditional security operations teams, Managed Security Operations Centers (SOCs), and Managed Security Services Providers (MSSPs) by bringing deeper and focused expertise in the analysis of threat indicators and the experience, tools, and processes for isolating security issues and eradicating them.
MDR is threat hunting and removal by elite security professionals.
The following are the salient points of MDR that business, mission and technology leaders should know:
- Detecting and Responding to cyber threats is a specialization not commonly found; it is difficult to invest in the required people/expertise, processes, and technology.
- SOCs/MSSPs and MDR providers have distinct and complementary characteristics that usually combine to provide the total operational solution for Cyber Security.
- MDR services are available to all types of organizations:
- Small or midsize organizations with minimal investments in security tools/staff.
- Well-invested organizations that need to augment their capabilities in this highly specialized niche.
- MDR providers should supply technologies, expertise and processes they require.
- Scrutinize how vendors are delivering services to ensure the technology stack and services will fit or can be molded to your environment.
- Prevention-focused security controls like firewalls and anti-virus are simply not enough to cope with today’s cyber threats. MDR actively hunts and contains threats that have bypassed all other security controls.
- MDR helps you meet stringent regulatory requirements, no matter your industry.
- Use MDR services to implement threat detection and incident response capabilities when they don’t exist or are immature, or when approaches such as MSS haven’t met expectations.
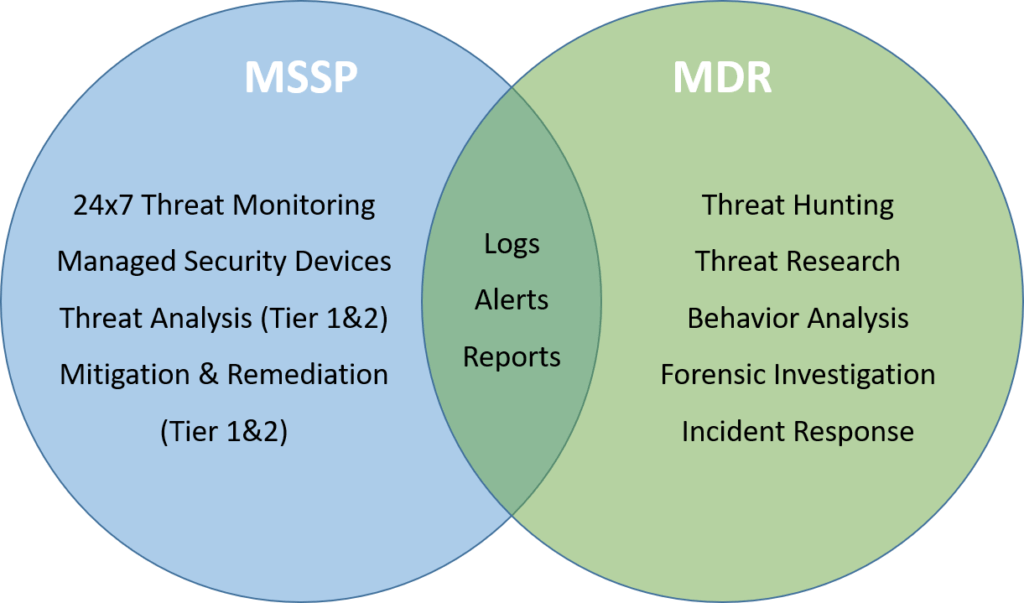
Difference Between a MSSP and a MDR
MDR services are characterized by the following attributes:
- Focuses on internal, lateral, and anomalous threat detection
- Uses the provider’s curated technology “stack”, deployed on a customer’s premises, which may include one or more tools, usually focused on network- and host-based solutions
- 24/7 monitoring, analysis, and customer alerting of security events with incident triage performed by a person (e.g., not relying just on automation to add some context to an event)
- Primary efforts are monitoring, hunting, and detecting data breaches, APT, and unauthorized access including internal threat actors through behavior analytics and data anomalies (versus SOC event correlation and alerting based on rulesets and reporting requirements)
- Includes incident validation and remote response services
- Typically, does not manage “security” hardware (e.g, firewalls, IDS, Endpoint software, etc.) except MDR aggregator/analytical systems
A Managed security service provider (MSSP) provides outsourced monitoring and management of security devices and systems. Common services include managed firewall, intrusion detection, virtual private network, vulnerability scanning, and anti-viral services. MSSPs use high-availability security operation centers (either from their own facilities or from other data center providers) to provide 24/7 services designed to reduce the number of operational security personnel an enterprise needs to hire, train and retain to maintain an acceptable security posture.
A MSSP usually maintains a fully provisioned security operations center (SOC) for security monitoring and response to ensure the client’s most critical data and services are protected.
- Provides central point of contact 24×7 for cybersecurity issues and support
- Establishes thresholds for events and alerts based on the client’s unique infrastructure
- Monitors events and alerts 24×7 using a centralized analysis system
- Responds to alerts by triaging suspicious activity and coordinating with the client for mitigation
- Monitors remote access requests for clients with telecommuting or external staff or customers
Managed detection and response (MDR) providers deliver services for buyers looking to improve their threat detection, incident response, and continuous-monitoring capabilities. In addition to security event monitoring focused on internet and network perimeter, ingress-egress traffic only, MDRs examine lateral (east-west) movement, once an attacker is inside the organization. MDR providers leverage advanced threat defense, along with security analytics, which can be expensive, difficult to obtain, and hard to sustain for many organizations, especially small or midsize businesses (SMBs) and small enterprises.
A MDR provides advanced persistent threat (APT) detection, insider threat, and threat intelligence capabilities for clients requiring more in-depth (tier 3 and above) security services.
- Enhanced intrusion detection
- Internal threat hunting and monitoring
- Insider threat detection
- Client incident response training exercises
- Full incident response and forensics services
CyberESI’s MDR Foundation
Our founders started their careers performing and managing thousands of Intrusions for the US Department of Defense and other Federal and Law Enforcement Agencies. They created a culture of teamwork, mentoring, continuous learning and sharing of threat intel.
Our leadership continues to staff our 24×7 Baltimore Operations Center with security analysts and incident responders equipped with advanced knowledge, forensic tools and approaches to combat today’s ever-evolving threat landscape, which means you get the highest levels of security, no matter the size of your organization.
Our purpose-built technology is continuously updated with the latest threat intel and analyzes suspicious activity in real time. Our technologies, inclusive of hardware and software, developed and refined over more than 10 years reduces Mean Time to Detection (MTtD) and Mean Time to Resolution (MTtR).
CyberESI’s MDR Architecture
CyberESI’s innovations are packaged in an appliance called Blackhawk. The Blackhawk is a purpose-built, multi-server and storage device housing software including our custom software.
The Blackhawk comes in 2U and 4U configurations with a unique server case containing two compute nodes and a storage array accessible to both nodes. The Blackhawk storage contains our proprietary solid state hard drives delivering high performance with the highest density in a long lasting device. The storage and servers allow us to capture, store, and analyze network traffic in excess of 10Gb per second.
The Blackhawk is running our proprietary network capture software with unique indexing and analysis technologies enabling CyberESI analysts to quickly query and inspect network packets without impacting capture and automated analysis processes.
The Blackhawk also facilitates software for log aggregation and analysis, systems for forensic investigations and our Intrusion Detection Software (IDS).

